
Forcepoint i500 Appliance
Cloud-Intelligent Appliance Provides Localized Control for Forcepoint Web Security Cloud Deployments

Click here to jump to more pricing!
Overview:
The Forcepoint i500 and i500v appliances complement Forcepoint Web Security Cloud deployment by adding flexibility and control over Web traffic flow for analysis, improving traffic speed in bottleneck locations and adding application and protocol control. Appliances can be deployed in select locations throughout a network to enhance traffic flow, user experience and policy enforcement.
Forcepoint Web Security Cloud deployments use cloud infrastructure for real-time analytics and threat protection. However, sending all web traffic to the Cloud may not always be in the best interest to your company. The Forcepoint i500 appliance or the virtual Forcepoint i500v appliance provide an innovative deployment option to analyze some traffic on-site, especially useful for organizations in countries with national firewalls, or to speed up traffic flow in offices experiencing heavy traffic volumes.
Why Choose The I500 OR I500V Appliances?
The Forcepoint i500 and Forcepoint i500v appliances complement a Forcepoint Web Security Cloud hybrid deployment by adding flexibility and control over web traffic flow for analysis, improving traffic speed in bottleneck locations, and adding application and protocol control. Appliances can be deployed in select locations throughout a network to enhance traffic flow, user experience and policy enforcement.
Localized control over cloud traffic
Deployed in conjunction with Web Security Cloud Gateway, the Forcepoint i500 and Forcepoint i500v appliance offer greater control over which traffic gets sent to the Cloud for analysis.
Intelligent use of the cloud decreases latency
- The Forcepoint i500 and Forcepoint i500v appliances use realtime cloud defenses when required to minimize on-site appliance footprint and investment.
- Benign web requests go “direct-to-net” for optimal performance and user experience, while suspicious requests or requests which need real-time content classification (e.g., Facebook) are sent to real-time cloud defenses for optimal protection.
Added application and protocol control
- Network Agent, included in both appliances, adds full-port monitoring capabilities to Web Security Cloud Gateway deployments.
- Network Agent enables monitoring of traffic outside of proxy analysis, and provides controls for hundreds of applications and protocols.
Industry-leading, real-time web security
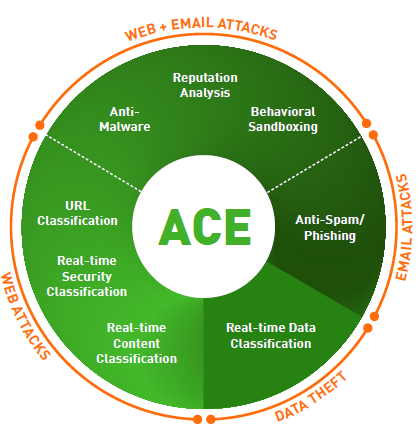
- Forcepoint Web Security solutions are powered by Forcepoint ACE (Advanced Classification Engine), which provides real-time protection by using eight defense assessment areas with over 10,000 analytics.
- ACE analytics are derived from the Forcepoint ThreatSeeker Intelligence, which unites more than 900 million endpoints and analyzes over 5 billion web requests per day for global threat awareness.
The Forcepoint difference: ACE (Advanced Classification Engine)
Forcepoint ACE provides real-time, inline contextual defenses for Web, Email, Data and Mobile security by using composite risk scoring and predictive analytics to deliver the most effective security available. It also provides containment by analyzing inbound and outbound traffic with data-aware defenses for industry-leading data theft protection. Classifiers for real-time security, data and content analysis — the result of years of research and development — enable ACE to detect more threats than traditional anti-virus engines every day (the proof is updated daily at http://securitylabs.forcepoint.com). ACE is the primary defense behind all Forcepoint solutions and is supported by the Forcepoint ThreatSeeker Intelligence.
Features and Benefits:
The Forcepoint i500 appliance provides fast on-box analysis for most traffic and cloud-based analysis for questionable requests. It is also available as the i500v virtual appliance.
I-Series Benefits:
- Deployed in conjunction with the Forcepoint Web Security Cloud, the i500 and i500v appliances serve as your “cloud on-ramp,” giving you greater control over which traffic gets sent to the cloud for analysis.
- Benign Web requests go “direct-to-net” for optimal performance and user experience, while suspicious requests or requests which need real-time content classification (e.g., Facebook) are sent to real-time cloud defenses for optimal protection.
- Network Agent, included in both appliances, adds full-port monitoring capabilities to Forcepoint Web Security Cloud and the Forcepoint Cloud Web Platform deployments.
- Network Agent enables monitoring of traffic outside of proxy analysis, and provides controls for hundreds of applications and protocols.
- Forcepoint Web Security solutions are powered by Forcepoint Advanced Classification Engine (ACE), which provides real-time protection by using eight defense assessment areas with over 10,000 analytics.
- ACE analytics are derived from the Forcepoint ThreatSeeker Intelligence, which receives up-to 5 billion endpoints daily from over 155 countries, resulting in threat intelligence that is applied in real-time by over 10,000+ analytics to stop threats across the threat lifecycle.
Advanced Defenses
- Scalable real-time contextual defenses surpass AV and URL filtering defenses, avoiding the trade-off of performance over security
Reduce Costs & Complexity
- Select appliance deployment throughout a Forcepoint Web Security Cloud deployment
- Deploy appliances only in select locations to decrease latency, localize control, or add application and protocol controls
Rely on Superior Cloud Service
- Global Data Centers (ISO 27001, ISO 27018, and CSA STAR certified)
- Industry-leading 99.999% SLA
Proven Forcepoint TRITON Architecture and Leadership
- TRITON architecture unifies web, email and data security with appliance, Cloud, software and hybrid deployments
- Over 20,000 customers worldwide
Specifications:
| G3 Hardware Specifications | |
|---|---|
| Capacity | Approx. 1300 TPS (h/w) , 1100 TPS (VM) |
| Processor | Intel Xeon E3-1231 v3 3.4GHz, 8M Cache, Turbo, 4C/8T, 80W, OEM XL |
| Chipset | Intel 3420 |
| Memory | 8 GB (2 x 4 GB) |
| HDD | 500 GB, SATA, 3.5-in, 7.2K RPM |
| On Board NIC | Broadcom 5720 Dual Port 1Gb LOM |
| Add on NIC | Silicom Dual Ports Copper Gigabit Ethernet PCI Express NIC |
| Power Supply | 250 W |
| Rails | Post Static Rails – DIB Kit included |
| Dimensions | 1U form factor, 15.5”D x 17.1”W x 1.67”H (39.37cm D x 43.10cm W x 42.6cm H) |
| Weight | Max. 17.76 lbs (8.058 kg) |
| Hardware Support | Globally available 24/7 by phone |
| Regulatory & Compliance | FCC / ICES / EN55022 / VCCIBSMI / C-Tick / SABS / CCC / MIC Class A and UL60950-1 / Verified to comply with RoHS Directive / Energy consumption and noise emissions in accordance with ISO 9296 |
| Virtual Appliance Hardware Requirements | |
| VMware ESXi 5.1 | Dedicated 4 cores and 12 GB RAM |
| VMware ESXi 5.5 | Optional Hardware bypass card for fault resilient installs |
Solutions:
| Feature | Description |
|---|---|
| Intelligent Hybrid Design | Intelligent security path analysis sends benign traffic direct-to-net for faster performance and better end-user experience, while utilizing real-time cloud defenses when required. It also provides more control over which traffic gets sent to the Cloud for analysis. |
| Network Agent | Provides hundreds of protocol and application controls. |
| Industry-Leading Security | Based on ACE, the same real-time, inline technology that protects many global corporations against unknown and advanced web threats. |
| Affordable Appliance | Provides the convenience of an appliance with the power of the cloud for a consistent and light on-site footprint. |
| Simple Installation and Operation | Deploys in less than one hour. Intuitive user interface enables quick policy and security setup as well as flexible reporting. |
Documentation:
Download the Forcepoint I-Series Appliance Datasheet (.PDF)
Pricing Notes:
- Pricing and product availability subject to change without notice.
