
Forcepoint Insider Threat
Deep Collection and Forensics for Unrivaled Visibility

Click here to jump to more pricing!
Overview:
Forcepoint Insider Threat has been identifying and stopping threats from within for government and Fortune 100 customers for more than 15 years. With more than 1 million endpoints deployed, Forcepoint Insider Threat’s proven solution protects some of the most sensitive organizations on the planet. One Fortune 100 retail client realized 60% ROI in the first year of deployment.
- Gain Visibility into Potential Insider Threats
Get a complete view of privileged users who interact with intellectual property and sensitive systems, and an archive of their actions through metadata, keystrokes, forensics, and video. - Prove Intent of User Actions
Investigate and remediate users with a rich history of user actions and live video replay that gives the context needed to prove or disprove malicious intent. - Identify Insider Threats to Critical Systems
An insider threat solution will monitor critical systems and analyze related user actions for risky behavior indicating potential fraud or cyber sabotage.
Forcepoint Insider Threat gives you unrivaled visibility into computer users’ early activity, helping you to stop data theft and loss by:
Detecting
Detecting suspicious activity, whether accidental or intentional.
Preventing
Preventing a hijacked system, a rogue insider or just a user making a mistake, ensuring that your intellectual property is not compromised.
Establishing
Establishing a normal behavior’ baseline, giving you early indications of a potential risk when a user begins to stray for their normal activity.
Providing Context
Providing context into a user’s behavior, aiding your investigation.
Identify
Automatically identify your riskiest users. An over-the-shoulder view enables you to put context around risky behavior. This lets you determine if the system was hijacked, the employee action was malicious, or if it was an accidental act.
Forcepoint Insider Threat Empowers Your Organization
Forcepoint Insider Threat saves you time and effort by automatically scoring and prioritizing your riskiest users, reducing the need to dig through thousands of alerts. This frees your team to focus on high priority tasks and improves efficiencies. Forcepoint Insider Threat also provides the context and forensic evidence needed for undeniable attribution and chain of custody – simplifying investigations, prosecution, and compliance.
Benefits:
No other vendor combines all of these advantages to defend your data against the threats from within in a single product.
- Only Forcepoint Insider Threat offers DVR capture and playback on both Windows and Mac OS endpoints.
- Our Command Center provides a highly intuitive way to identify the riskiest users and quickly see patterns that can uncover broader risk.
- Forcepoint Insider Threat provides granular control over when to collect data and what to specifically gather to protect users’ privacy.
- Only Forcepoint Insider Threat integrates with Forcepoint DLP to help you quickly drive to smarter remediation decisions after risky behavior is detected.
Key Features:
Forcepoint is the only vendor to provide these key insider threat defense features in a single product.
- Metadata collection and aggregation to baseline user and workgroup behaviors, enabling you to later automatically detect when a user strays into abnormal behavior.
- Integration with Forcepoint DLP, providing the forensics capabilities you need to quickly drive to smarter remediation decisions after risky user behavior is detected.
- Alert aggregation quickly identifies the riskiest users.
- Video collection and playback helps expedite investigation, allowing for attribution as well as showing employee intent and is admissible in a court of law.
Use Cases:
Anticipate Data Theft
Quickly identify data theft behavior indicators (ex. frequent visits to job boards, updating resumes, or stockpiling data) to prevent exfiltration when employees separate from the organization.
Protect Employees from Workplace Harassment
Monitor verbal attacks on employees through communication channels such as social media, email, and instant messaging to prevent incident escalation.
Achieve Contractor Oversight
With Forcepoint Insider Threat, you can also ensure that temporary employees are using appropriate resources to get their work done and not violating terms of their agreement.
Features:
Built from the Ground Up to Detect Insider Threat Activity—Accidental or Intentional
Complete Visibility into User Actions for Insider Threat Detection and Forensics
Get a complete view of user actions with a lightweight, highly scalable agent and integrated third-party data.
Investigations with Full Video Replay
Workflows tie together relevant user activity and sources of risk with event timelines, trend lines, and access to precise user activity—including live video capture and replay of individual user actions.
Intuitive User Interface with Prioritized Risk Actors
Make quick decisions to mitigate risk of insider threats with a sequential listing of activity leading up to and following event.
Behavior Risk Scoring Engine
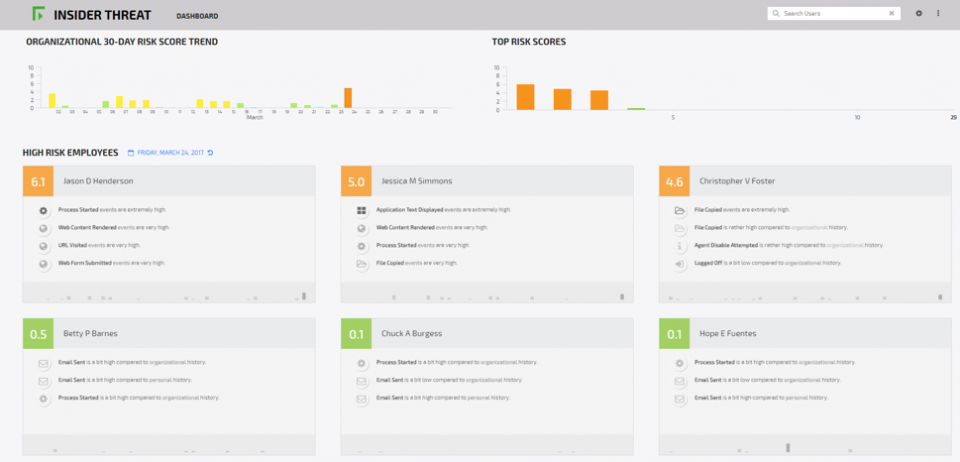
Baselines behaviors for individual users and work groups, identifies anomalies, and provides a daily consolidated risk score for each user. Quickly highlights your organization’s 30-day risk trends.
Prevent Abuse While Respecting Privacy
Anonymize the individual during risk scoring while retaining the ability to connect a user to their individual actions when enterprise risk is at stake. Governance to control, monitor, and audit investigators.
Active Threat Mitigation and Data Protection via Forcepoint DLP integration
Apply data classification from Forcepoint DLP to risk scoring and investigations while applying active data containment for best-in-class data protection.
Capabilities:
Built as an insider threat solution, Forcepoint Insider Threat is not an existing solution retrofitted to the problem – it’s a unique and unrivaled security tool designed specifically to protect your data from malicious or accidental threats. Forcepoint Insider Threat’s development was headed by a team of domain security experts who have spent their careers in information protection.
Forcepoint Insider Threat delivers these unmatched data protection capabilities:
- Protects against unintentional insider threats as well as malicious insider behavior.
- Video replay provides full behavioral context to rapidly discern malicious from benign actions, easily reviewed and understood by non-technical personnel – all while respecting employee privacy guidelines through customizable, business-driven policies.
- Analytics prioritizes users who have anomalous behavior and provides deep visibility into their actions, including past behaviors.
- Integrated, enterprise-wide system – no need to buy or maintain a number of independent software applications.
- Distributed architecture prevents performance impact.
- Proven, stable, lightweight agent.
- Data collection from multiple sources, including Forcepoint DLP.
- Detects risky behavior even when users are off the corporate network.
Solution Components:
Analtyical User Behavior Risk Scoring Engine
- Forcepoint gives you the visibility needed to have early warning signs that users have been hijacked, gone rogue, or are just making mistakes – before sensitive data gets breached or stolen.
- Forcepoint Insider Threat saves you time and effort by automatically scoring and prioritizing your riskiest users, reducing the need to dig through thousands of alerts.
- The Forcepoint Insider Threat Command Center provides a highly intuitive way to identify the riskiest users and quickly see patterns that can reveal broader risks.
- Forcepoint Insider Threat video capture and replay capability gives you unparalleled visibility into suspicious behaviors before they become problems (e.g., creating back doors, stockpiling data).

How Forcepoint Insider Threat gives you Insider Threat Protection
- Baselines both individual and organizational behavior across channels to understand what behavior is normal and expected.
- Searches for anomalies in an individual’s behavior to detect potential insider threats (both intentional and unintentional).
- Provides a consolidated user risk score for each user on each day, as well as quickly highlighting 30 day risk trends.
- Simplifies the investigation process by prioritizing risky users.
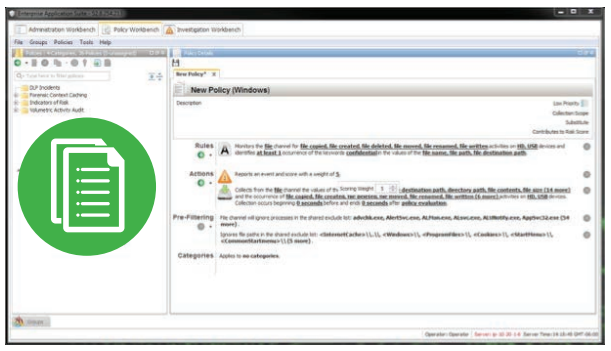
Policy-Driven Identification of Risky Behavior
- Customers can define specific behaviors that are known to be risky, based on a set or sequence of activities.
- These policies allow for detection of a wide range of activity monitoring from PII and HIPAA compliance requirements to IP protection and limited malware detection.
- These customer-specific policies weigh into the overall risk score.
- Customers can manually tune the weighting of these policies to adjust the level of their contribution to the overall risk score.
Visualization Showing Risk Score Contributors
- For each user on each day, an intuitive chart is generated allowing an investigator to quickly understand what types of activities caused them to receive a high risk score.
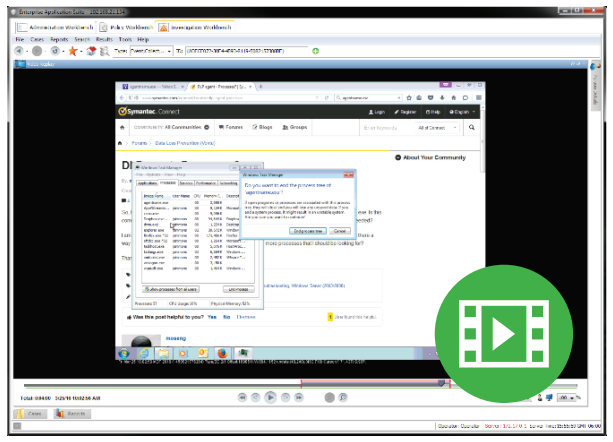
DVR-Like Desktop Video Replay
- Screen shot captures and play back provide an over-theshoulder view, giving you unparalleled visibility into suspicious behaviors before they become problems.
- Policies provide you with the context and the evidence needed to attribute an incident to a user and to determine if they have been hijacked, gone rogue, or are just making mistakes.
- Investigators can easily call the desktop video replay for high-risk users and view any suspicious activity, with userattribution that is admissible in a court of law.
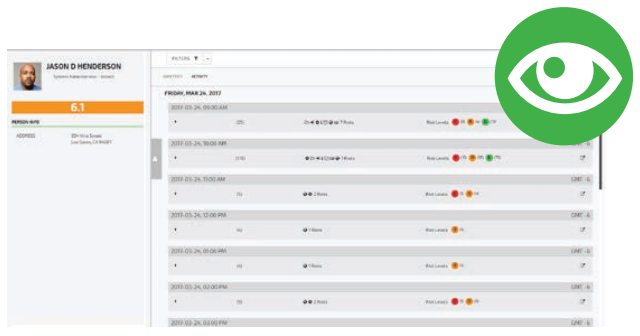
Timeline Activity Review and Additional Forensic Details
- The Forcepoint Insider Threat Command Center saves you time and effort by automatically scoring and prioritizing your riskiest users, reducing the need to dig through thousands of alerts.
- An easy drill down into the risky user and an expandable timeline, showing you the actual acts that the user is doing to that is making them a risky user.
- Record and playback gives you visibility into the user’s intent and simplifies the investigation process.
- Provides you with the context and content around users’ actions, helps with attribution and aides in the prosecution of malicious behavior.
Screenshots:
Documentation:
Download the Forcepoint Insider Threat Datasheet (.PDF)
Pricing Notes:
- Pricing and product availability subject to change without notice.
