
Forcepoint Cloud Access Security Broker (CASB)
Complete Security for all Cloud Applications Period

Click here to jump to more pricing!
Overview:
Forcepoint CASB Cloud Access Security Broker discovers cloud application use, analyze risk, and enforce appropriate controls for SaaS and custom applications.
- Complete Visibility Into Shadow IT
Identify and categorize cloud apps to access risk and pinpoint which services to allow and monitor with Forcepoint Cloud Access Security Broker (CASB). - Prevent Compromised Accounts
Stop bad actors from accessing cloud application data. Use leading machine learning and UEBA capabilities to establish behavioral fingerprints for advanced risk calculation. - Secure Mobile Access to Cloud Apps
Apply unique access and security policies on a per-device basis by easily distinguishing between managed and unmanaged (BYOD) devices.
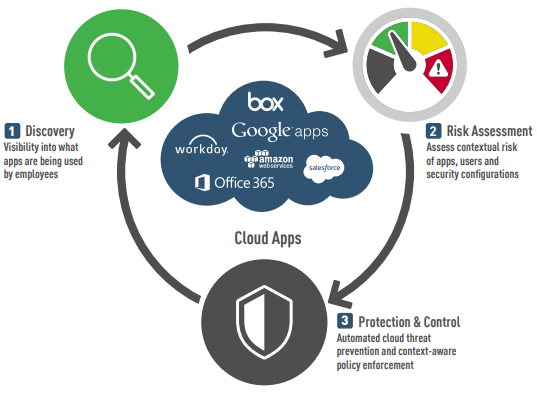
Forcepoint CASB offers enhanced security for data in cloud apps, so your end-users can access their favorite apps without restriction.
The Forcepoint CASB value
- Discover and risk-prioritize all unsanctioned cloud use (Shadow IT) to quickly and easily determine if applications meet governance rules and avoid compliance issues
- Unleash the power of BYOD with improved employee productivity and cost savings while ensuring security of employees and corporate resources in the cloud
- Identify anomalous and risky user behavior in the cloud to stop malicious users, as well as clamp down on user activities that don’t meet best practices
- Reduce the risk of exposing sensitive cloud data to unauthorized users in violation of governance and regulatory rules
- Identify potentially inappropriate privilege escalation to prevent the impact associated with root account takeover
- Implement geo-location-based access and activity monitoring for legitimate users and malicious actors
- Track application usage for compliance, licensing, and cost savings of unused accounts
DLP Integration
Forcepoint CASB integrates with DLP solutions to provide unified data protection extending from on-premises to the cloud environment. It also integrates with solutions such as web security, email security, next-generation firewall and more.
Built in Cloud UEBA
Forcepoint CASB creates a risk profile based on threat likelihood and business impact. It utilizes analytics based on thousands of apps and activities to provide risk prioritized alerts for SOC and incident response teams.
Bring Your Own Device (BYOD)
Forcepoint CASB has the most comprehensive use case coverage, with API and forward/reverse proxy support. This provides granular device and activity control for unmanaged devices.
Cloud Monitoring and Control for any app
Forcepoint CASB has flexible product architecture to support any application, including custom applications, without product changes. Users can fully audit and protect application usage in a matter of hours or days.
Quick Time to Value
Choose from best of both worlds with API and Proxy Mode to expedite implementation and reduce risk in your cloud environment.
One CASB Platform. Multiple Cloud Applications. Multiple Integrations. Better Results.
Eliminate security blind spots by following the rhythm of your people and flow of your data. Forcepoint CASB can support any cloud application with multiple key partner integrations.
ArcSight
Splunk
Q1 Labs
Okta
Ping Identity
AirWatch
MobileIron
Office 365
Box
Salesforce.com
Microsoft Azure Information Protection
G-Suite (Google Drive)
Slack
ServiceNow
Use Cases:
Industry-Leading Data Loss Prevention
Forcepoint DLP integration prevents cloud application data leakage without redefining policies.
Better Control of Your Cloud App Admin
Delegate administrative privileges for high-risk activities such as making global access changes and enabling multi-factor authentication of admin and privileged user permissions.
Control Sharing of Sensitive Files
Enable productive collaboration with third parties in SaaS environments without accidentally exposing critical files that contain sensitive data such as PII, financial records, and protected IP with CASB.
Intelligent Threat Detection
Use deep inspection to automatically detect and block malicious executables from being stored in cloud applications with Advanced Malware Detection.
Quick and Easy Security for Cloud Apps
Secure any cloud application (SaaS, PaaS, IaaS, or homegrown) without waiting for us, whether you are using APIs or inline (proxy) with Cloud Access Security Broker.
Location-Based Access Controls
Enable access restrictions based on user/cloud service location to help comply with data regulations with CASB.
Features:
Forcepoint CASB Eliminates Security Blindspots
Security for All Cloud Applications
Forcepoint CASB's unique proxy analysis engine gathers information from a broad set of activities to build mapping files for cloud apps, enabling support for any cloud app.
Cloud Application Risk Scoring
Categorize the overall risk for each cloud application based on regulatory requirements, industry certifications, or your own internal benchmarks.
Automated App Catalog and Risk Updates
Maintain your cloud application security posture with automatic updates to cloud application catalog and changes in risk properties as soon as they become available.
User Governance
Quickly identify dormant/orphaned accounts and external users to reduce operational costs and minimize associated security threats.
Integrated Remediation Workflow
Utilize a unique built-in organizational workflow to assign and complete risk mitigation tasks via Forcepoint CASB or through integration with third-party ticketing systems.
Automatic Anomaly Detection
Forcepoint CASB's unique cloud-based UEBA continuously monitors user behavior to detect anomalous activity, so you can quickly identify and stop high-risk insider or external attacks.
Device and Location-Based Access Control
Enable unique policies for managed and unmanaged devices, whether they're on browsers or rich mobile applications. Implement access restrictions based on the location of the user or cloud service.
Cloud Application Discovery
Utilize existing log files to automate the discovery and categorization of cloud applications within your enterprise with Forcepoint Cloud Access Security Broker.
Advanced and Customizable Risk Metrics
Establish detailed cloud application risk posture metrics and information for each application to strengthen your overall security posture, with the option to create customizable weightings.
Data Classification
Catalog and identify sensitive or regulated data, including file sharing permissions and stored in file-sync services to ensure compliance with regulations like PCI, SOX, HIPAA.
Application Governance
Benchmark your cloud application security configurations against industry best practices and regulatory requirements (PCI DSS, NIST, HIPAA, etc.) to identify security and compliance gaps.
Real-Time Activity Monitoring/Analytics
Understand potential exposure with real-time activity monitoring and analytics by user (regular, privileged users, admins), group, location, device, application action, and more.
Data Loss Prevention
Data classification at rest with real-time content inspection and action for data residing in cloud applications.
Integration With Third-Party Solutions
Forcepoint CASB security offers integration with leading SIEM, Identity Access Management, and Mobile Device Management solutions, providing a seamless holistic solution to protect cloud applications.
Solution Components:
| Feature Description | Cloud Governance | Cloud Protection | Cloud Security Suite |
|---|---|---|---|
| Application Visibility & Risk Assessment (available in API deployments) | |||
| Cloud App Discovery — Leverage existing log files to automate discovery and categorization of cloud apps used | |||
| Cloud App Risk Scoring — Rate overall risk for each cloud app based on regulatory and industry certifications and best practices | |||
| Cloud App Usage Summary — Includes number of users, activities, traffic volume and typical usage hours for each cloud application | |||
| Advanced Risk Metrics — Detailed cloud app risk posture metrics and information for each application | |||
| Customizable Risk Metrics — Detailed cloud app risk posture metrics with customizable weightings | |||
| Continuous Discovery — Schedule automated scanning of log files and generation of discovery reports on a periodic basis | |||
| Centralized Discovery Dashboard — Aggregated discovery results, current usage baselined against prior activity, and usage trends | |||
| App Catalog & Risk Updates — Automatic updates to cloud app catalog and changes in risk properties as they are available | |||
| Activity Log Collections — Collect basic activity logs for users and privileged users via cloud app APIs | |||
| Account & Data Governance (available in API deployments) | |||
| Data Classification — Identify and catalog sensitive or reg. data to ensure regulatory compliance (e.g., PCI, SOX, HIPAA) | |||
| User Governance — Identify inactive or orphaned accounts (e.g., ex-employees), and external users (e.g., contractors) to reduce operational costs/minimize security threats | |||
| App Governance — Benchmark security configurations against a set of industry best practices/regulatory reqs. (e.g., PCI DSS, NIST, HIPAA) | |||
| Integrated Remediation Workflow — Leverage built-in org. workflow to assign/complete risk mitigation via Forcepoint CASB or through 3rd-party ticketing systems | |||
| Real-time Activity Monitoring & Analytics (available in inline/proxy) | |||
| Activity Monitoring & Analytics — Real-time activity monitoring and analytics by user, group, location, device, application action, and more | |||
| Privileged User Monitoring — Real-time activity monitoring and reporting of privileged users and admins | |||
| Enterprise SIEM Integration — Adaptors to directly feed activity logs into leading SIEM solutions, including ArcSight, Splunk, and Q1 Labs | |||
| Automatic Anomaly Detection — Continuously monitor behavior and detect anomalous activities, including high-risk insider and external attacks | |||
| Real-Time Threat Prevention — Correlate activity anomalies with risky IP addresses to alert, block, quarantine, or verify ID for app or spec. within an app | |||
| Data Leak Prevention — Data classification at rest and real-time content inspection for more than 100 file types and hundreds of pre-defined data types (e.g., PCI, PII, PHI, HIPPA, SOX) | |||
| Multi-Factor Authentication — Risk-based identity verification when anomalous or high-risk activities are detected | |||
| Single Sign-On — Leverage built-in or 3rd-party SSO to access SAML-based apps | |||
| Dynamic Alerts — Real-time notifications for policy violations or activity thresholds via SMS/email | |||
| Mobile & Endpoint Access Control — Unique policies for managed and unmanaged devices, whether originating from browsers or rich mobile apps | |||
| Location Based Access Controls — Restrict access based on the location of the user or the location of the cloud service | |||
| MDM Integration — Leverage existing MDM deployment to manage endpoint enrollment and cloud access | |||
| Custom Policies — Visual policy editor enables easy configuration of custom policies based on various attributes | |||
| Advanced Cloud Architecture | |||
| Performance Optimization — Accelerate access to cloud apps through the caching and content optimization | |||
| Centralized Threat Intelligence — Unified view of threats to enterprise database tables, files stored in file shares, and data stored in cloud apps | |||
| Admin. & Access | |||
| SIEM Integration — Generate discovery data in Common Event Format for integration with existing SIEM environments | |||
| Enterprise Directory Integration — Use existing AD or LDAP directory infrastructure for user, group, and organizational reporting and policy | |||
| Role-Based Admin — Define permissions for editing assets, policies, and system settings | |||
| Enterprise Reporting — Flexible reporting options including pre-defined reports with the ability to edit and save customized reports | |||
| Encryption Broker — Bring your own key (BYOK) or encryption to cloud service providers, with Forcepoint CASB handling the key rotations and providing full audit | |||
Screenshots:
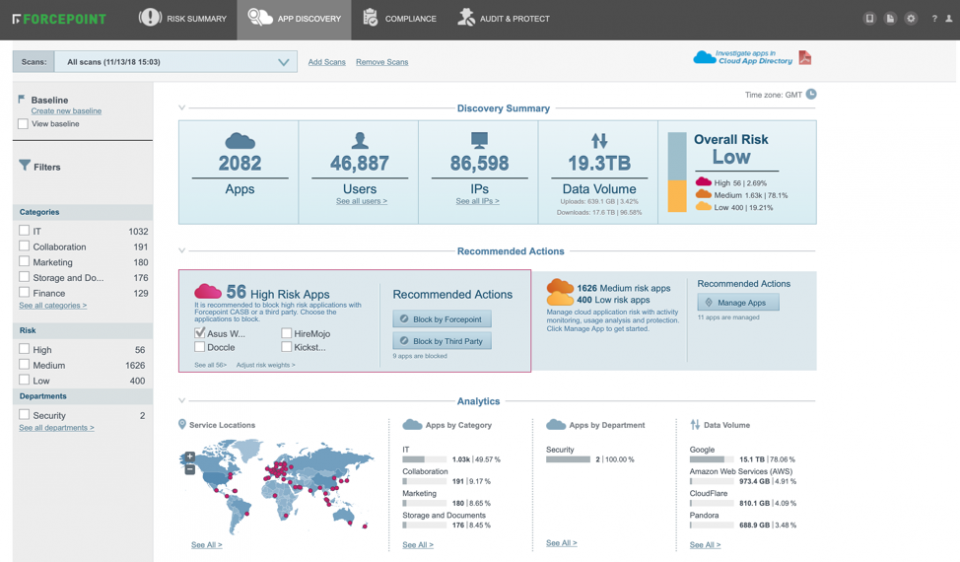
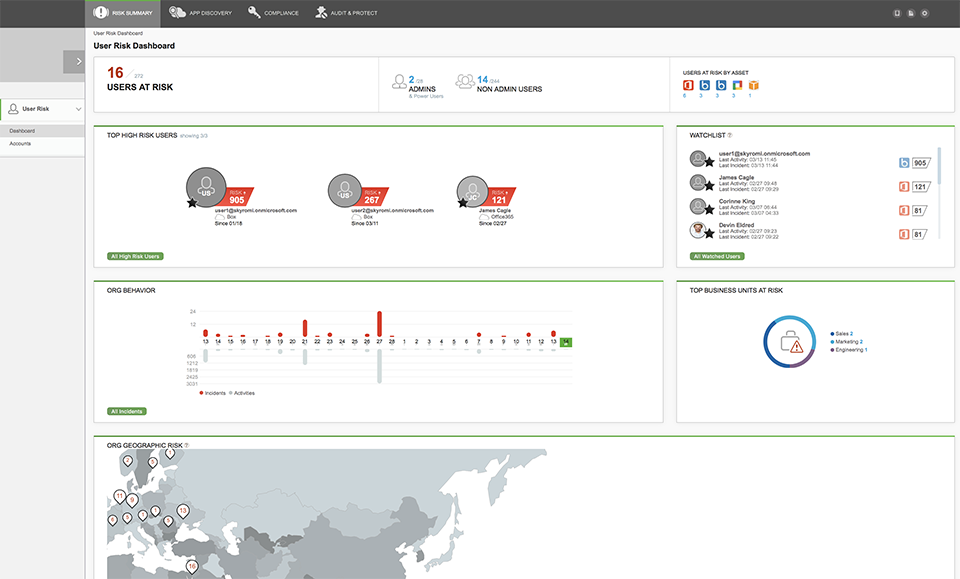
Documentation:
Download the Forcepoint CASB Cloud Access Security Broker Datasheet (.PDF)
Pricing Notes:
- Pricing and product availability subject to change without notice.
