Forcepoint User and Entity Behavior Analytics (UEBA)
AI-Fueled Behavior Analytics to Identify Real Entity Risk

Click here to jump to more pricing!
Overview:
As the threat landscape continues to evolve, security leaders responsible for protecting data are turning to behavior analytics to prevent data exfiltration from accidental, malicious, and compromised users. Forcepoint user and entity behavior analytics (UEBA) is a powerful behavior analysis platform that enables security teams to proactively monitor for high risk behavior.
Forcepoint UEBA’s market-leading platform integrates structured and unstructured data to provide holistic visibility into nuanced human activity, patterns, and long-term trends that comprise human risk. The product offers a variety of customer use cases through a diverse set of analytics built upon four tenets: Diverse Data Sources, Hybrid Analytics, Configurability, and Transparency
- Identify Potential Sources of Data Exfiltration and Critical IP Loss
Determine users exhibiting risky behavior such as stockpiling and atypical data movement before critical IP leaves your organization. - Advanced Compromised Account Detection
By understanding attributes like typical access patterns, prevent bad actors from accessing your critical assets and systems with User and Entity Behavior Analytics (UEBA). - Be a Partner to Human Resources
Analyze communications-based data sources to identify potential code-of-conduct infractions.
Diverse Data Sources
Forcepoint UEBA is a powerful platform with a defined generic data model, flexible enough to handle incredibly diverse data yet structured enough to apply powerful big data analytics. The product’s information model provides specific guidelines for how to map data from different sources in order to maximize the effectiveness of the analytic engines.
- The flexible data model, in combination with the detailed information model, enables security operation operatives and analysts to integrate existing and future security products without the need for new product releases or data scientist intervention.
- Organizational data sources such as data loss prevention (DLP) tools, security information and event management (SIEM) tools, and even HR applications are examples of relevant data sources.
- Traditional UEBA platforms integrate with a static set of data sources. Updates to these platforms require downtime and the expertise of engineers and data scientists.
Hybrid Analytics
Traditional security approaches are rule (policy) driven, with hundreds, thousands, or even tens of thousands of pre-defined patterns used to identify known bad activity. Such rule-based approaches are attractive because they allow experts to encode knowledge about specific bad activities, yet are limited in their effectiveness.
When new threats emerge, users must act quickly to create corresponding policies. Additionally, policy- or rule-based approaches are not able to detect subtle, risky behavior. For example, if a person logs in from an unusual location and copies sensitive documents they haven’t recently accessed, this may constitute risk even if it doesn’t violate a policy. Forcepoint UEBA employs both rule-based and statistical disciplines by combining the two into a hybrid analytic approach that is far more effective than either approach alone.
The Forcepoint UEBA Analytic Hierarchy (shown in Figure 1) is made up of features, models, and scenarios:
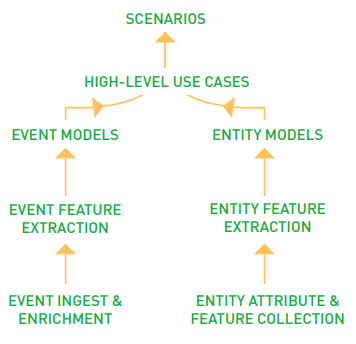
Figure 1. Forcepoint UEBA Analytic Hierarchy
Features are bits of information extracted from individual events that may make a person or their activity interesting: they can represent behavioral patterns (e.g., the hour of day, destination domain, or applications used); they may be related to data characteristics (e.g., file type, file size, classification, or sentiment); they may be personspecific (e.g., role, office location, administrative access privilege levels, or results from a performance review). Forcepoint UEBA automatically learns the distribution of feature values across event datasets, which enables it to use artificial intelligence approaches to recognize anomalies and calculate risk.
Features are used to define models, which are also statistical- and data- driven. Models compute summary statistics to describe an entity’s activity over time. Forcepoint UEBA models are unique in that they provide either partial or, in some instances, full access to the underlying analytics and engine. A model may measure, for example, the number of bytes uploaded to a cloud storage site, the number of unique printers accessed, or how anomalous a user’s web search activity is relative to his or her own past or against an organizational baseline. All raw model scores are normalized with respect to prior observations, and users or analysts can utilize their learned expertise of the organization.
Finally, Forcepoint UEBA scenarios correspond to high-level use cases and consist of several models. One example is the Data Exfiltration scenario, which combines a variety of model scores that may indicate an employee is leaking data.
Configurability
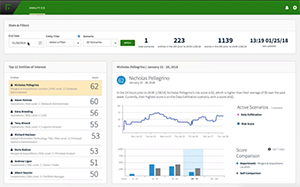
Not only does Forcepoint UEBA use a hybrid approach to analytics, effectively combining domain expertise with the power of artificial intelligence, but the encoding of domain expertise is exposed to all administrative UEBA users. Forcepoint UEBA sets itself apart from competitors in that it allows application end-users or analysts to contribute their own domain expertise about their organizations, their data, and their people. Security risks vary widely across organizations, depending on the industry, region, and standard business practices. Raw event model scores contributing to an entity scenario’s risk score are shown on an entity timeline and the events that contribute the most to those model scores are shown clearly
Forcepoint UEBA empowers security operations analysts to contribute their own expertise to build their own use cases, manage and build their own analytics, and develop analytical use cases without the help of engineering or support service groups. Users may configure and tune additional features, models, or scenarios all through the user interface. Lexicons allow customers to easily customize and manage keywords and phrases such as project code names. Customers also have the flexibility to enable additional privacy controls for lexicon deemed highly confidential to certain business units such as HR or Legal.
Transparency
The analytics in Forcepoint UEBA are simple and easy to understand, producing accurate and insightful results. Unlike competitor UEBA products, Forcepoint UEBA provides transparency by exposing enhanced detail so analysts can understand how the user community works and then add their own expertise to the features and models.
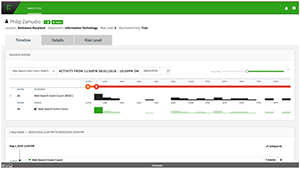
For example, an analytics administrator can change the scoring weight of a cloud storage upload or weekend activity based upon the data feeds from various data sources, such as the organization’s SIEM or DLP tool set. When the analyst investigates a user of interest, they do so through the user-friendly entity timeline, which provides analytic explanations and context, allowing the analyst to make informed judgments and take appropriate actions as they assess possible security threats.
Summary
Organizations want to avoid data security incidents to stay out of the headlines, and therefore choose behavior analytics to protect data from accidental, malicious, and compromised users. Forcepoint UEBA protects sensitive client information, detects compromised accounts, and enforces the continued improvement of an organization’s internal security culture.
Organizations that choose Forcepoint UEBA to improve their security posture gain many benefits, including:
- Comprehensive Visibility. Forcepoint is the only vendor that covers structured and unstructured business data in addition to communications to leave no detection gaps.
- Deep Context. Focus on behaviors, not just anomalies, with precise narratives that indicate unwanted behavior.
- Flexibility. Easily build or customize risk models to fit any unique organization and support any risk use case.
- Efficiency. Pivot from alert to investigation with in-depth analytics within a single platform.
The broadest set of data ingest sources in the UEBA security market—including structured and unstructured data sources
Data may be sourced from anywhere within the organization. Below are just a few examples of those systems:

Use Cases:
Get More Out of Your SIEM Investment
UEBA adds context and analytics to SIEM data and provides risk scoring to incidents organized by entity, allowing analysts to prioritize the highest risks.
Perform Context & Content-Rich Incident Response
Enable transparent comprehensive investigation with advanced analytics like machine learning and artificial intelligence that are tuned toward specific behavior risk.
Solve Challenges in Data Security and Regulatory Compliance
Analyze and detect patterns of human behavior in big data, delivering insights into enterprise risk where threats have surpassed the perimeter.
Features:
Uniquely Powerful Analytics to Achieve Situational Awareness
Automate DLP Policy Enforcement
Combine UEBA with Forcepoint DLP to utilize analytic risk scores to dynamically change DLP policies.
Configurability
There is no one-size-fits-all UEBA solution. Forcepoint allows customers to build their own use cases and develop their own analytics without the need of a data scientist.
Detect Seemingly Unrelated Threats
Single alerts lack context to data. UEBA uses natural language processing and sentiment analysis for a holistic view of the user.
Transparency
Understandable analytics with simple explanation and context to make informed decisions about possible insider threats.
Entity Timeline
View all historical activity during forensics stage with dynamic visualization.
Varied Dataset Calculations
Data models informed by both structured data, such as SIEM logs, and unstructured data, such as email and chat, from your disparate security tools and third-party applications.
Platform Architecture:
From Data to Behavior Insights - Functional Architecture
The Forcepoint User and Entity Behavior Analytics (UEBA) platform is a distributed, fault-tolerant, fullstack application that enables deep visibility into your critical data streams for identifying enterprise insider risks. The purpose of this document is to provide an understanding of the major components within the Forcepoint UEBA application, how they contribute to the overall Forcepoint UEBA solution, and specific technical benefits of these components.
As described below, and illustrated on the following page, raw data from a multitude of sources flows into the Ingest Architecture, and finally into the Application layer, where enriched Forcepoint UEBA events are persisted, analyzed, and presented to analysts for investigative review.
Architecture Layers
Layer I: Data › Forcepoint UEBA collects raw data from a wide variety of enterprise data feeds, including communications, physical access, endpoint, and network activity. Forcepoint DLP and Forcepoint Insider Threat are recommended—but not required —data sources.
Layer II: Ingest › In the Ingest layer, raw data feeds are transformed and prepared for analysis. Leveraging a flexible data collection platform (i.e., TCP listener, FTP download), Forcepoint UEBA gathers raw data, transforms to Forcepoint UEBA’s event format, and passes data through its ingest pipeline and analytics engine.
Layer III: Application › The Application layer provides massively scalable data storage and querying capabilities, runtime behavior analytics, an analyst and administrator interface, as well as an outbound API.
Forcepoint UEBA Analytics Framework
Forcepoint UEBA’s analytic approach is founded on three core elements that establish: what can and should be captured; how to capture activity and enrichment information; and which analytic models to run to identify insider risk. Each element is briefly described below.
Audit Guidance › Recommends the ideal logging and collection settings given a customer’s network and security ecosystem.
Information Model › Ensures the consistency of data mapping across very different data sources.
Baseline Analytic Models › Provides out-of-the box analytic configurations of features, models and scenarios.
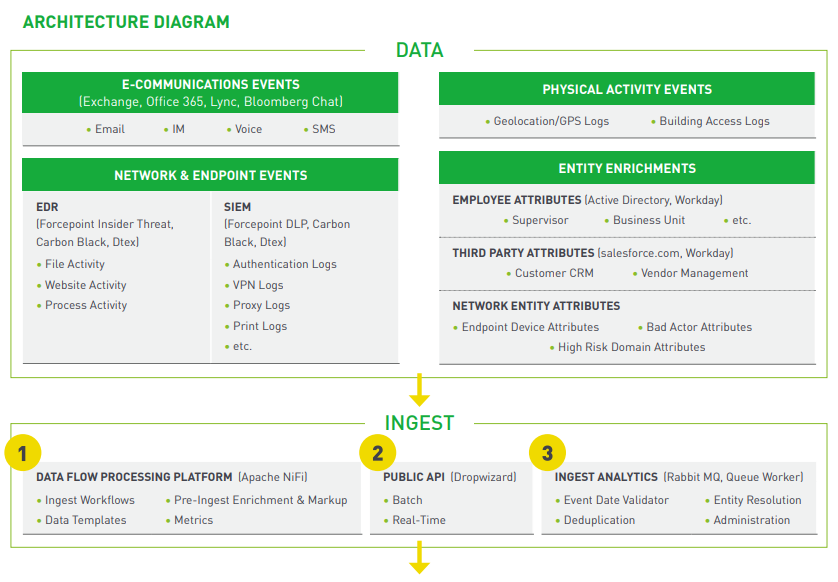
Layer I: Data Processing Platform
Forcepoint UEBA relies on feeds from an organization’s existing sensors, logs and network security fabric to deliver its insider threat behavioral analytics. To consume raw data, Forcepoint UEBA’s Data Processing Platform leverages a range of collections mechanisms which can include listening for incoming TCP or UDP streams (i.e., syslog), API queries (i.e., Splunk API), or batch data pulls using FTP, file share access, etc.
Layer II: Ingest
The first set of components in the platform handles data ingest and enrichment. Once the types of data to be analyzed in Forcepoint UEBA are determined, as prescribed by the Audit Guidance, those data sources are mapped to the Information Model in the pre-ingest dataflow processing platform. They are then ingested into Forcepoint UEBA via the Public API and are finally piped through a series of enrichment and analytic processes. Each of these components and their benefits are discussed below.
1. Pre-Ingest Data Flow Processing Platform › Forcepoint UEBA primarily uses the Apache NiFi framework for processing data prior to ingest into the platform. Originally developed by the National Security Agency, Apache NiFi moved to open source in 2014. The key concepts of the NiFi framework—data provenance, transformation, loose coupling, high concurrency, metrics—align closely with Forcepoint UEBA’s ingest objectives, and the productized Forcepoint UEBA/NiFi solution provides customers with a set of workflows, templates, and processors, for datasource consolidation and publishing to the Forcepoint UEBA Public API, that are standardized, hardened and resilient. The data flow processing platform also enables customers to develop and implement environment-specific enrichment processors for marking up events prior to ingest in Forcepoint UEBA, so data feeds can be customized without the added cost of Forcepoint UEBA professional services. In summary, the pre-ingest data flow processing platform provides additional extensibility and flexibility without introducing added cost or complexity.
2. UEBA Streaming Ingest Public API › The Forcepoint UEBA Public API is a RESTful API used for ingesting event and entity information into the application, either in real-time or via bulk upload to the API. The API contains numerous convenience endpoints that align with the Information Model mappings (also used in the preingest data flow processing platform), and also offers a standardized set of metrics that measure request latencies. Convenience and visibility into ingest are two primary benefits offered by the Public API. (Note: Certain data sources can be placed directly into the ingest pipeline discussed below, but Forcepoint UEBA strongly recommends use of the Public API.)
3. UEBA Ingest Pipeline (Validation › Enrichment › Analytics) › Once event and entity information is ingested via the Public API, it is placed on the Message Queue and into the Queue Worker for further processing and enrichment. Each of the processors in the queue worker ultimately provides benefits downstream for analytics and forensic investigation. Let’s look at each:
- Event Date Validator: Enables Forcepoint UEBA to ingest only events that are relevant to the configured analytic time window
- Deduplication: Allows for removal of duplicate events so they do not create noise and unnecessary work for users in the application
- Entity Resolution: Provides resolution of identifiers on an event to a specific entity, so that a single entity can easily be tied to multiple identifiers and modes of activity
- Disclaimer Detection: Removes analytically uninteresting text, namely disclaimers, from communications events so that they do not generate noise in the system
- Labeling: Racilitates labeling of events based a defined set of policies
- Feature Scoring: Represents the first building block in our analytic process, by scoring every event based on the configured set of Baseline Analytic Models loaded into the system
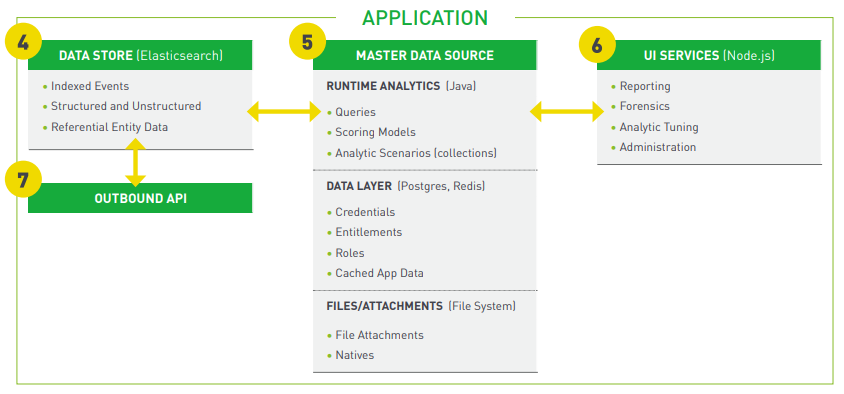
Layer III: Forcepoint UEBA Application
Once events and entities are ingested into the system, they are then stored for use in the application. This section outlines the functions and benefits of each component in the application itself.
4. Data Store › Forcepoint UEBA uses ElasticSearch (ES) as the primary data store for event and entity information. Elasticsearch is proven at scale and provides significant end-user benefits for text search, analytics and aggregation that other database technologies simply cannot provide.
5. Master Data Service (MDS) › Forcepoint UEBA’s proprietary Master Data Service provides much of the application’s analytic capability and also correlates data from within the Elasticsearch data store to other supporting technologies (e.g., Postgres and Redis are used to store relational and transactional data). One advantage of that separation of data stores is the ability to scale them independently of each other, allowing for more deployment configuration controls based on users monitored and data ingested, and ultimately lower operational expense for our customers.
- Runtime Analytics: These analytics enable the execution of ad hoc, real-time analyst queries, entity-centric risk score calculations and scenariobased user behavior analysis (i.e., data exfiltration, privileged user abuse, and flight risk scenario-based analytic rollups).
- Data layer: User credentials, entitlements and roles are stored in the Master Data Service. Additionally, cached application data is maintained here, speeding query response times.
- Files/Attachments: For those event feeds which include files and attachments, the Master Data Service indexes the contents of those files for attachments, and optionally persists the original attachments for easy end-user access and drill-down from the user interface. This vastly improves analyst productivity by allowing an integrated forensic deep dive, directly from a scored event.
6. UI Services › Forcepoint UEBA’s user interface layer is a web application, whereas the client is a browser. A server running node.js HTTPS is used for all browser/ server interactions, Redis for caching application data, as well as user sessions.
7. Outbound API › Lastly, Forcepoint UEBA provides an Outbound API service that allows external applications to retrieve processed events and their associated analytic metadata (i.e., Feature and Models). This enables customers to leverage Forcepoint UEBA’s analytic findings in other systems (i.e., security orchestration or workflow).
Key Architecture Takeaways
In summary, the Forcepoint UEBA ingest and application stack uses a variety of well understood and highly respected open source technologies, combined with proprietary solutions, in order to offer the following technical differentiators and benefits for our customers:
- Modern, scalable architecture that grows horizontally as data volumes grow
- Flexible entity and event data model that is “baked into” the Forcepoint UEBA ingest pipeline, which can consume, resolve and analyze both structured and unstructured data, and allows for rapid integration of new feeds
- Pipelined data processing that sequences content classification, event scoring, risk modeling and behavioral profiling
- Highly configurable real-time analytics allow Forcepoint UEBA to tackle a variety of use cases, from rogue trading to market manipulation to data exfiltration and corporate espionage
- Real-time query engine allows ad hoc, analyst-driven investigation and behavioral analytics
Information Security:
Protect IP, Detect Compromised Accounts and Reduce Insider Risk
Forcepoint User and Entity Behavior Analytics (UEBA) enables security teams to proactively monitor for high risk behavior inside the enterprise. Our security analytics platform provides unparalleled context by fusing structured and unstructured data to identify and disrupt malicious, compromised and negligent users. We uncover critical problems such as compromised accounts, corporate espionage, intellectual property theft, and fraud.
Why Forcepoint UEBA for security
Our clients rely on us to deliver context about human behavior inside the enterprise. Only Forcepoint UEBA offers configurable analytics to help security analysts tackle the problems that matter most to the business. We are built to scale while helping security teams:
- Reduce the time to detect insider attacks
- Surface relevant alerts at a time when security teams are drowning in noise
- Get granular about insider activity, going beyond SIEM and other tools in your stack
- Improve investigation efficiency for incident response and post-breach forensics
Platform Pillars
Forcepoint UEBA provides insight into high-risk behaviors and individuals, not just anomalous alerts. By evaluating nuanced interactions between people, data, devices and applications, Forcepoint UEBA prioritizes timelines for security teams. Our software is built upon four pillars:
- Rich Context › Fuses disparate data sources into a single narrative, combining communications content to decipher intent alongside SIEM, endpoint and employee enrichment feeds.
- Behavioral Analytics › Applies multiple types of rigorous behavioral and content-based analytics focused on change, pattern, and anomaly detection to better detect sophisticated attacks.
- Search & Discovery › Exposes powerful forensic search and discovery tools through a context-rich user interface for ongoing monitoring and deep-dive investigations.
- Intuitive Workflow › Delivers proactive reporting that fully integrates with human workflow and existing client information architecture to streamline operational efficiency.
Redefining Security Analytics
Context-Driven Visibility › Forcepoint UEBA uniquely delivers visibility into employee activities, behaviors and relationships by integrating unstructured, context-rich data streams with structured data. Our analytic models allow entities and events to be scored and prioritized through multiple lenses across all data streams — previously unavailable to security teams. We also integrate with Active Directory, SIEM, EDRs, and key data sources to offer true situational awareness, and a powerful forensic platform that radically enhances internal investigations.
Configurable Analytics › Traditional, black-box UBA tools are often limited to structured data sources, analyzed in disparate systems, with a fixed configuration of analytics. Forcepoint UEBA, in contrast, delivers powerful analytic capabilities that allow security teams to address evolving security use cases, and to perform real-time ad hoc analysis, including advanced search across all data sets. Our analytics can be tuned without additional programming, allowing a more nimble response to security threats.
Scale › We are fundamentally built to scale. Only Forcepoint UEBA uses ElasticSearch to power instant access to massive amounts of data. Our platform seamlessly stores both structured and unstructured data and scales horizontally to grow with our clients. Forcepoint UEBA also provides variable levels of access and administrative controls so you can rely on our technology to work for your business in any type of deployment.
Capabilities
- Roles-Based Dashboards and Workflows
Enable rapid review of non-compliant activity through an intuitive user interface so analysts and managers can quickly investigate, review, escalate, and take action. - Robust Data Entitlements
Fully support complex data entitlements required by both internal controls and externally driven data privacy concerns. - Extensible Platform
Configurable analytics, dashboards, usergroups, and workflow support out-of-the-box security use cases with full capability to expand to any risk use case. Flexible privacy controls provide confidentiality between workgroups. Delivers advanced data science models without a heavy professional services commitment. - Flexible Deployment Options
Readily deploy Forcepoint UEBA on-premise, in a virtual private cloud, or even using a Forcepoint UEBA appliance.
Advanced Analytics
- Behavioral Analytics
Identify changes in behavior that may indicate current or potential illegal, unwanted or non-compliant activity by employees using sentiment and content analysis. - Intelligent Prioritization
Prioritize events of interest and alerts based on the analysis of content and metadata patterns. - Natural Language Processing (NLP)
Significantly reduce false positives through a smart, practical application of NLP, complex lexicons for any language, and text identification technology that recognizes disclaimers and quoted text from threaded emails. - Visualizations
Tailored visualizations specifically developed to unlock an analyst’s own inference capabilities and deliver maximum context around relevant activities. Quickly understand the who, what, when, and how of employee actions. - Content Classification
Supercharge DLP deployments using Forcepoint UEBA’s content classification engine to identify and filter out non-relevant communications like bulk mail, 3rd party
Regulatory Surveillance:
Meet your compliance obligations more effectively and with fewer resources
Join the revolution of industry-leading banks, hedge funds, and asset managers using Forcepoint User and Entity Behavior Analytics (UEBA) to more precisely identify employees engaged in bad behavior—whether illegal, non-compliant, or posing a reputational risk— and speed both initial review and deeper investigation. Forcepoint UEBA creates the most targeted set of employees and events for review, and then gives compliance teams the most intuitive and context-rich interface from which to triage, escalate, and resolve alerts as necessary.
Why Forcepoint UEBA
- Identify employees that are putting the organization at risk
- Reduce the cost of surveillance
- Respond quickly to regulators
Platform Pillars
Forcepoint UEBA provides insight into high-risk behaviors and individuals, not just high-risk events. By evaluating nuanced interactions between people, data, devices and applications over time, Forcepoint UEBA prioritizes timelines for compliance teams. Our software is built upon four technical pillars:
- Full Context › Fuses disparate data sources into one platform, including communications content, trade activity and alerts from existing trade monitoring systems, and employee enrichment feeds.
- Sophisticated Analytics › Applies multiple types of rigorous behavior and content-based analytics focused on change, pattern, and anomaly detection.
- Search and Discovery › Exposes powerful forensic search and discovery tools through a context-rich user interface for ongoing monitoring and deep-dive investigations.
- Intuitive Workflow › Delivers proactive reporting that fully integrates with human workflow and existing client information architecture.
How Forcepoint UEBA is reshaping the cost of surveillance
Optimize Workflow › Forcepoint UEBA is radically reshaping organizational workflow in two big ways. First, organizations are able to adopt a more strategic supervisory structure that efficiently distributes work across front office supervisors, compliance teams, and audit functions. Second, the capability to see all relevant data in one place—without waiting multiple days for it to be retrieved from various silos by IT personnel— significantly increases day-to-day monitoring and indepth investigations.
Replace Costly, Ineffective Technology › Forcepoint UEBA’s modern “big data” architecture is highly scalable to cover more employees, data, and use cases than legacy technology. In addition, the capability to support sophisticated analytics, house all relevant data, and provide real-time search results across the platform is foundational to unlocking analyst efficiency.
Enterprise Capabilities
- Roles-Based Dashboards and Workflows
Enable rapid review of non-compliant activity through an intuitive user interface so analysts and managers can quickly investigate, review, escalate, and take action. - Robust Data Entitlements
Fully support complex data entitlements required by both internal controls and externally driven data privacy concerns. - Platform Flexibility
Configurable and out-of-the-box analytics, dashboards and workflow adapt to any risk use case and bring advanced data science models to you without a heavy professional services commitment. - Flexible Deployment Options
Readily deploy Forcepoint UEBA on-premise, in a virtual private cloud, or even using a Forcepoint UEBA appliance.
Advanced Analytics
- Behavioral Analytics
Identify changes in behavior that may indicate current or potential illegal, unwanted, or noncompliant activity by employees. - Feature Tagging and Modeling
Prioritize events of interest based on the analysis of both content and metadata patterns found in specific events using domain expertise and advanced probabilistic models. - Natural Language Processing (NLP)
Material reduction in false positives through a smart, practical application of NLP supporting complex lexicons, including text identification technology that recognizes and zones out disclaimers and quoted text from earlier emails in a chain. - Visualizations
Tailored visualizations specifically developed to unlock an analyst’s own inference capabilities and deliver maximum context around relevant activities. Quickly understand the who, what, when, and how of employee actions. - Content Classification
Dramatically reduce the number of eComms for review by leveraging Forcepoint UEBA’s classification engine to identify and filter out non-relevant communications like bulk mail, sell-side research, 3rd party mailers and more.

Discover and Stop Insider Threat:
Forcepoint UEBA's uniquely powerful analytics find malicious insiders no matter how they try to hide
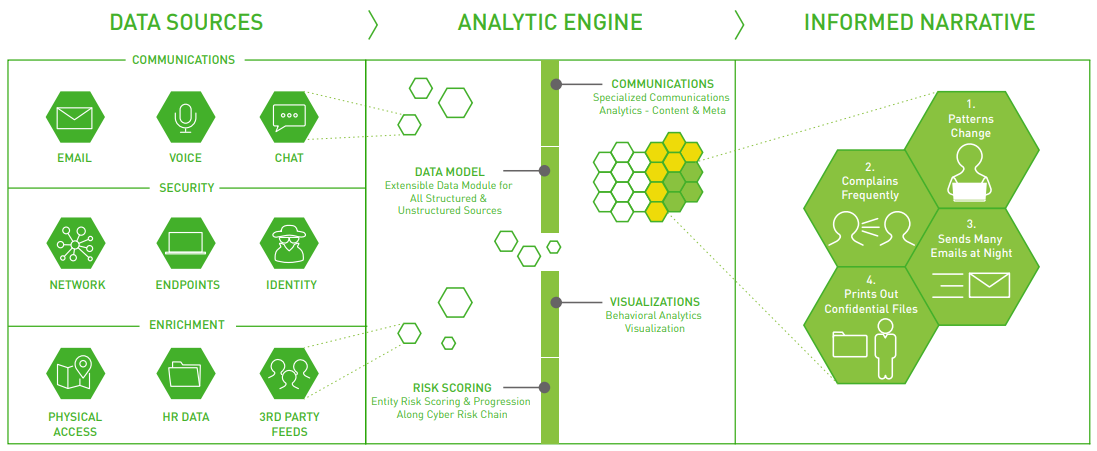
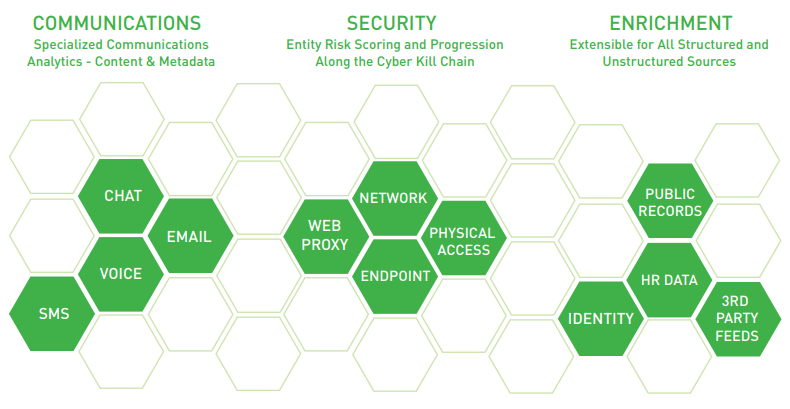
The insider threat spans an overwhelming landscape. It is nearly impossible to achieve situational awareness while at the same time quickly identifying specific threats. The Forcepoint User and Entity Behavior Analytics (UEBA) Insider Threat platform leverages a uniquely powerful analytic framework that pierces through the fog by looking across all insider activity, factoring in the intrinsic risk of each insider and supplementing activity streams with value-add information from across a company’s security and compliance ecosystem.
The Unique Power of Forcepoint UEBA's Analytics
Synthesize Across All Human Activity
- The Forcepoint UEBA Platform takes all human activity—communications, financial, physical, systems/ digital—and analyzes it to identify unwanted activity.
- Forcepoint UEBA leverages raw activity data as well as value-add signals from other security tools in the ecosystem, including DLP alerting.
Fully Incorporate Intrinsic Human Risk
- Each insider has their own level of intrinsic risk given attributes such as their role, tenure, location, performance and more. Leverage these data to raise or lower the risk assessment across each insider’s activity.
- In addition to internal stores of knowledge on people, Forcepoint UEBA can leverage on-going assessments and information from outside sources (e.g., public records).
Leverage “Out-of-the-Box” and Refine & Extend with Ease
- Forcepoint UEBA’s platform ships with its industry leading analytic models for identification of threats such as data exfiltration, malicious users, compromised users, negative behavior and more. Each model has been developed and successfully deployed against real world threats.
- Forcepoint UEBA customers are able to leverage these off-the-shelf models and can refine and extend them as use cases and threats evolve. These capabilities are available without the need for data scientists, engineers, or expensive professional services.
Analytics are “Understandable” and “Explainable”
- Today’s insider threat teams need the ability to fully understand and explain the analytics that identify potentially malicious insiders. Forcepoint UEBA’s analytics are fully explainable to support discussions with Legal and Compliance, ultimately enabling swift investigation and action.
Operational Overview
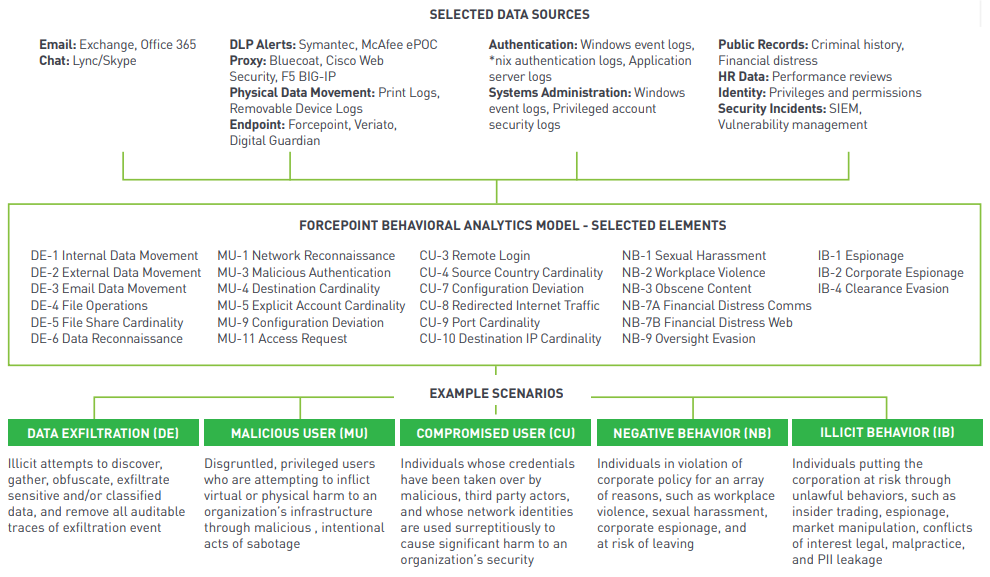
Forcepoint UEBA integrates readily with communications, security, and other enterprise applications currently in use. Forcepoint UEBA’s built-in, proprietary behavioral analytics models analyze information from across the across the enterprise to generate a holistic view of behavioral risk:
Documentation:
Download the Forcepoint UEBA User & Entity Behavior Analytics Datasheet (.PDF)
Pricing Notes:
- Pricing and product availability subject to change without notice.