Forcepoint Dynamic Data Protection
Protect your data and enable your people to get the job done

Click here to jump to more pricing!
Overview:
Prepare for the next level in user and data security with the integration of the market’s most powerful endpoint and user behavioral analytics. Forcepoint Dynamic Data Protection significantly reduces time to discovery, holistic forensic investigations, and alert burdens caused by false positives, allowing you to quickly respond to risk while maintaining optimum business efficiencies.
Digital transformation, cloud, and mobility have driven information technology to an inflection point and security architectures to a breaking point. As a result, organizations struggle to empower their mobile workforce, maintain the right application for the task at hand, and provide proper protection for data as it flows throughout the environment. Traditional approaches to data protection leave systems drowning in alarms and alerts and security organizations struggling to review and triage security content, adjust system policies, and remediate risk.
Now, there is a smarter way to safeguard your sensitive networks and data, no matter where they reside or are accessed. Integrating behavior-centric analytics with data protection tools, Forcepoint Dynamic Data Protection allows you to identify high-risk activity and automate policies to protect data in near realtime, providing the highest security with the greatest end-user productivity.
Risk-Adaptive Security Driven by Analytics
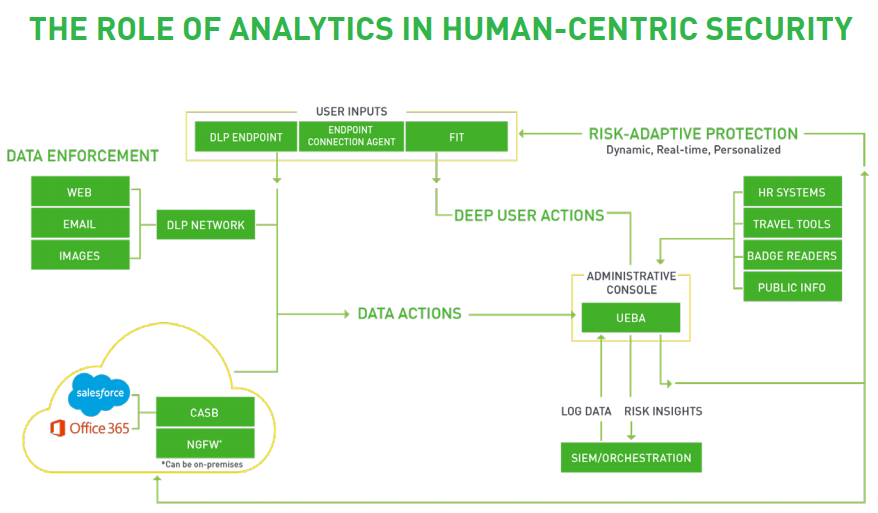
At the forefront of delivering adaptive security, behavior-centric analytics ingests data from traditional security systems and nontraditional data sources, and then combines them for a richer picture of context around the end users within an organization. By fusing data from traditional security systems and output from data loss prevention with that of other organizational sources (e.g., HR, travel logs, email and chat communication), you get a more informed contextual picture on behavior to quickly identify anomalies within that picture.
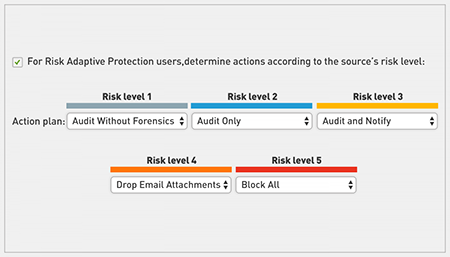
Using this context, analytics directs enforcement toolsets to adapt policies automatically based on changes in risk levels, providing Risk-Adaptive Security to your organization. Risk-Adaptive Security automatically responds to risk and adapts policies down to an individual user level—controlling data and access on-premises, on endpoints, and in the cloud.
Introducing Dynamic Data Protection
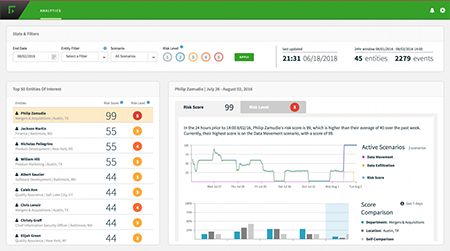
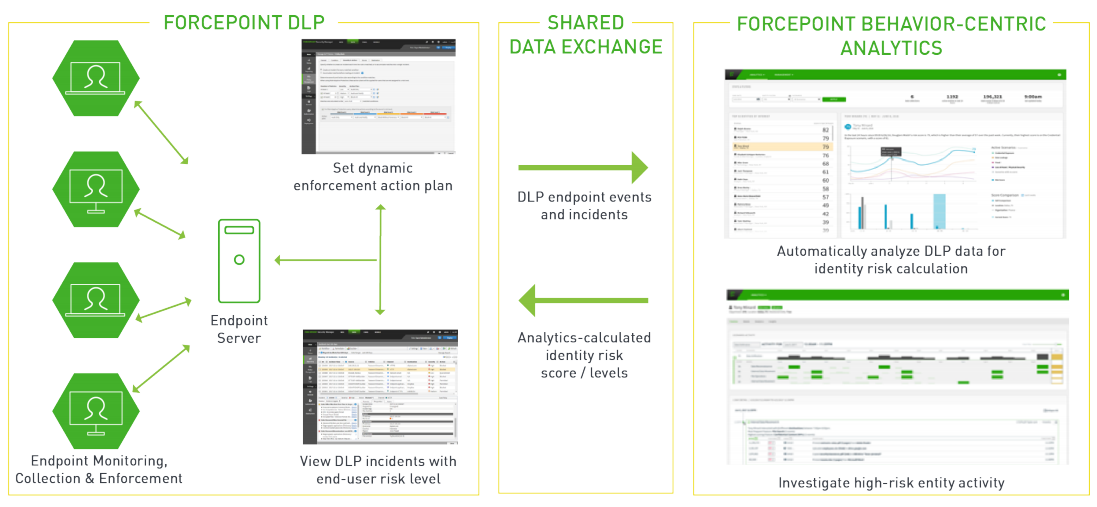
Dynamic Data Protection delivers a system for identifying and investigating entities that post potential risk to critical data and assets. It dynamically applies monitoring and enforcement controls to protect assets based on risk level of actors and the value of data.
DLP and Behavior-centric Analytics combine to create Automated Policy Enforcement:
- Behavior-centric Analytics profiles high risk user activity based on DLP incidents, data models, and endpoint collector events.
- Behavior-centric Analytics dynamically allocates a risk score to entities based on user activity.
- DLP applies automated controls to user interactions with sensitive data based on their current risk level.
- Behavior-Centric Analytics supports detailed investigation of high risk user activity.
Use Cases:
Unbalanced Strategy
Over-restrictive policies cause headaches and avalanches of alarms, and under-restrictive policies leave you exposed.
Too Many False Alerts
Unintegrated security solutions detect digital activities, but can’t reveal high-risk events. You find out too late to stop breaches.
Intervention is Manual
Analysts spend too much time determining if investigation is needed.
Features:
Only Forcepoint shifts the approach to proactive, dynamic security—without the headaches
Individualized, adaptive security
Replace broad, sweeping rules with individualized, adaptive data security that won’t slow down your employees.
- Each individual has a unique and variable risk level, informed by behavior-centric analytics.
- Risk levels are driven up and down based on user behavior and interaction with data.
- Changes in risk levels continuously drive enforcement for an individual.
Block actions only where you need to, and drive a more productive organization forward.
Analytics-driven forensics
Unify discovery, analysis, and enforcement, improving investigation efficacy and drastically reducing the rate of occurrence.
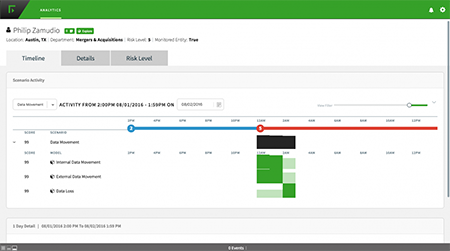
- Utilizing the baseline of normalized behavior, uncover abnormal internal/external data access and file movement that matches a compromised credential event.
- Automate manual processes, transitioning from broadly applied policies to ones at an individual level, unifying enforcement.
- View a narrative that provides context such as detailed timeline events, resulting in more efficient investigation practices.
- Detect precursor behaviors and potential high-impact incidents before they occur, preventing data loss.
Automate policy enforcement
Dynamic Data Protection surfaces anomalies, and proactively adjusts individualized data security controls in near real-time to protect your data.
- Automatically enforce policies with graduated response.
- Allow behaviors for low-risk individuals and take stronger action as risk levels are elevated.
- Reduce manual decision-making and overall alert volume.
How It Works:
The product orchestrates risk insights with adaptive enforcement to remove the need for human intervention.
By using Dynamic Data Protection, organizations can solve the fundamental challenges of traditional DLP deployments and more effectively protect sensitive information, including regulated data sources and PII. This is first and only solution in the market of its kind, and the only one that can automate policy enforcement to dynamically respond to changes in risk within an organization. With intelligent analytics, unified policy, and orchestration at its core, only Forcepoint can provide the end-to-end, human-centric security architecture required for the security challenges of today and tomorrow.
Documentation:
Download the Forcepoint Dynamic Data Protection Datasheet (.PDF)
Pricing Notes:
- Pricing and product availability subject to change without notice.